Cyberwarfare

What Is Cyberwarfare?
From stealthy espionage to critical‑infrastructure disruption, cyberwarfare has reshaped how nations compete, defend, and project power. Cyberwarfare is the use of digital operations by nation‑states (or their proxies) to achieve political, military, or strategic objectives against other states. Unlike financially motivated cybercrime, these operations are designed to shape the geopolitical environment—from covert data theft to overt disruption of critical services.
In cyberspace, borders are porous, timing is instantaneous, and plausible deniability is a strategic weapon.
Strategic Objectives
- Espionage -Stealing sensitive diplomatic, military, and commercial intelligence to inform strategy, negotiations, and technology development.
- Disruption – Temporarily degrading command‑and‑control, media, financial services, or logistics during crises to gain leverage.
- Destruction – Damaging data, systems, or industrial equipment (e.g., ICS/OT) to reduce adversary capability at critical moments.
- Psychological & Influence Ops – Shaping public narratives, trust, and morale via coordinated information operations, botnets, and synthetic media.
- Deterrence Signaling – Demonstrating offensive reach and credible consequences to dissuade rivals from escalation.
Anatomy of a Cyberwarfare Campaign
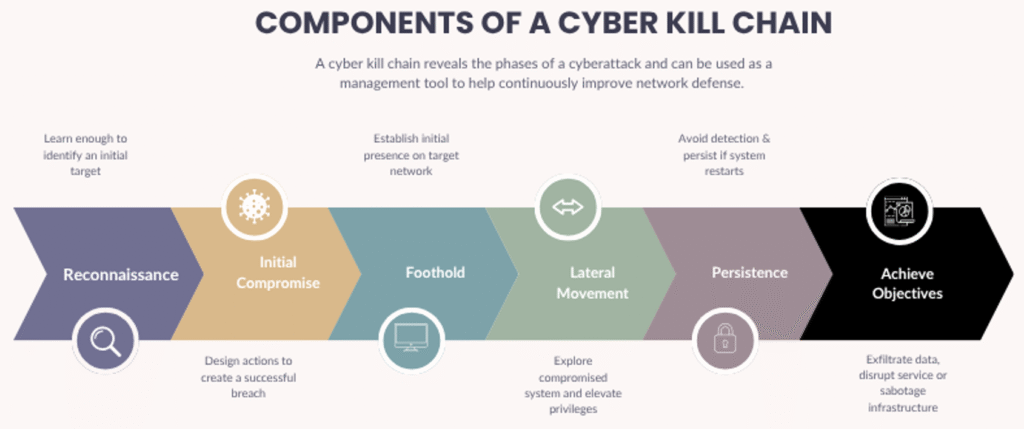
Nation‑state operations rarely hinge on a single exploit. They unfold as multi‑phase campaigns aligned to a kill chain or attack chain, designed for persistence, privilege, and precision. Components of a cyber kill chain typically include:
- Reconnaissance: OSINT, infrastructure mapping, tech‑stack fingerprinting, and human profiling.
- Initial Compromise: Exploiting N‑days/zero‑days, spear‑phishing, or supply‑chain injection.
- Establish Foothold: Dropper/loader, web shells, EDR evasion, initial C2 beacons.
- Lateral Movement: Credential theft, Kerberoasting/Pass‑the‑Hash, abusing misconfigurations and trusts.
- Maintain Presence: Multiple persistence mechanisms, staging infrastructure, log tampering, LotL.
- Achieve Objective: Data exfiltration, service disruption, ICS manipulation, or timed effects.
Tactics, Techniques, and Procedures (TTPs)
- Zero‑Day & N‑Day Exploits: Rapid weaponization and deployment preceding patch cycles.
- Watering‑Hole Compromise: Poisoning high‑traffic sites used by target communities.
- Credential Operations: Spear‑phishing, token theft, MFA fatigue, and session hijacking.
- Command‑and‑Control (C2): Multi‑layered, redundant C2 with domain fronting and fast‑flux DNS.
- Living off the Land (LotL): Abuse of built‑in admin tools (e.g., PowerShell, WMI) to blend with normal ops.
- Payload Modularity: Swappable implants, plugins for discovery, exfiltration, and ICS/OT actions.
Cyberwarfare vs. Traditional Warfare
| Aspect | Cyberwarfare | Traditional Warfare |
|---|---|---|
| Visibility | Covert, deniable; hard attribution | Visible forces and materiel |
| Tempo | Seconds to minutes; continuous | Weeks to months to deploy |
| Geography | Borderless; global reach via networks | Bound by terrain and logistics |
| Cost | Lower relative to kinetic operations | High (personnel, platforms, sustainment) |
| Casualties | Economic/psychological; physical possible via ICS/OT | Direct human casualties likely |
Case Studies
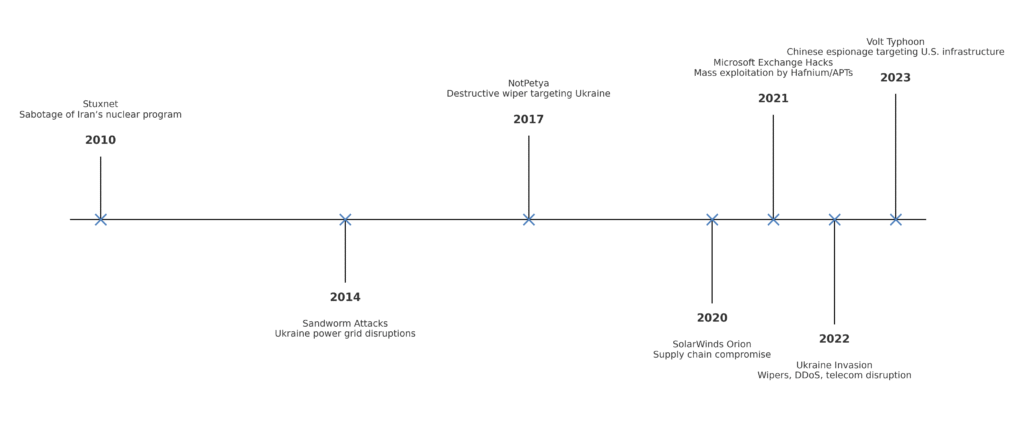
Stuxnet (2010)
A precision ICS operation that sabotaged nuclear enrichment by manipulating centrifuge speeds—one of the earliest public examples of cyber‑physical effects.
NotPetya (2017)
A destructive wiper masquerading as ransomware, seeded via software updates in Ukraine; collateral damage ran into the billions globally.
SolarWinds Supply‑Chain Compromise (2020)
Tampered software updates created a trusted pathway into government and enterprise networks, demonstrating the systemic risk of supply‑chain trust.
Russia–Ukraine (2014–present)
Blended playbook of DDoS, wipers, phishing, and satellite/telecom disruption underscores the role of cyber as a constant accompaniment to kinetic conflict.
The Attribution Problem
Attribution is a technical, analytic, and political challenge. States leverage:
- Proxies & Contractors: Semi‑deniable operators with variable control.
- False Flags: Deliberate TTP mirroring to implicate other actors.
- Global Infrastructure: Botnets and leased VPS across neutral jurisdictions.
The result is a persistent “gray‑zone” where action stays below the threshold of declared war yet achieves strategic impact.
Law & Ethics
International law is catching up. The Tallinn Manual helps interpret how existing law may apply, but there is no binding, universal treaty defining bright‑line norms for state behavior in cyberspace. Issues include:
- When does a cyber incident constitute an armed attack?
- Is kinetic retaliation proportional to non‑lethal cyber effects?
- How should civilian infrastructure and data be protected?
Defense & Deterrence
Whole‑of‑Nation Cyber Defense
- National Cyber Agencies: Sector guidance, advisories, incident coordination.
- Public–Private Partnerships: Joint exercises, tabletop simulations, red‑team support.
- Threat Intel Sharing: Rapid IOCs/TTPs dissemination, ISAC/ISAO networks.
Operational Resilience
- Zero Trust Architectures: Identity‑centric access, continuous verification.
- Segmentation & Hardening: OT/IT separation, SBOMs, least privilege, secure‑by‑design.
- IR & Recovery: Tested runbooks, immutable backups, chaos drills, RTO/RPO objectives.
Practical takeaways:
- Adopt assume breach mindsets; instrument for detection and rapid containment.
- Prioritize identity protection: phishing‑resistant MFA, conditional access, key management.
- Monitor for LotL behavior; baseline administrative tooling to spot anomalies.
- Harden the software supply chain: code signing, SBOMs, dependency auditing, CI/CD guardrails.
- Exercise executive decision paths for cyber crisis—before you need them.
What’s Next: The Future of Cyber Conflict
- AI‑Accelerated Ops: Faster reconnaissance, exploit discovery, and adaptive C2—matched by AI‑assisted defense.
- Post‑Quantum Risk: Harvest‑now‑decrypt‑later against sensitive traffic; crypto‑agility becomes mandatory.
- Space & Satellites: Attacks on comms, PNT, and imaging constellations expand the attack surface beyond Earth.
- Synthetic Media: Deepfakes weaponize perception; authenticity pipelines (content provenance) become critical.
Expect cyberwarfare to precede, accompany, and outlast kinetic phases of conflict.
FAQ
Further Reading