Darknets / Dark Web
Introduction
When the term darknet comes up, most people imagine shadowy corners of the internet where cybercriminals thrive. While this perception is not entirely inaccurate, it only tells part of the story. Darknets play a complex role in today’s digital ecosystem. For cybersecurity practitioners, researchers, and policymakers, understanding darknets is essential—both for defense against criminal activity and for appreciating their role in digital privacy, free speech, and political resistance.
What is a Darknet?
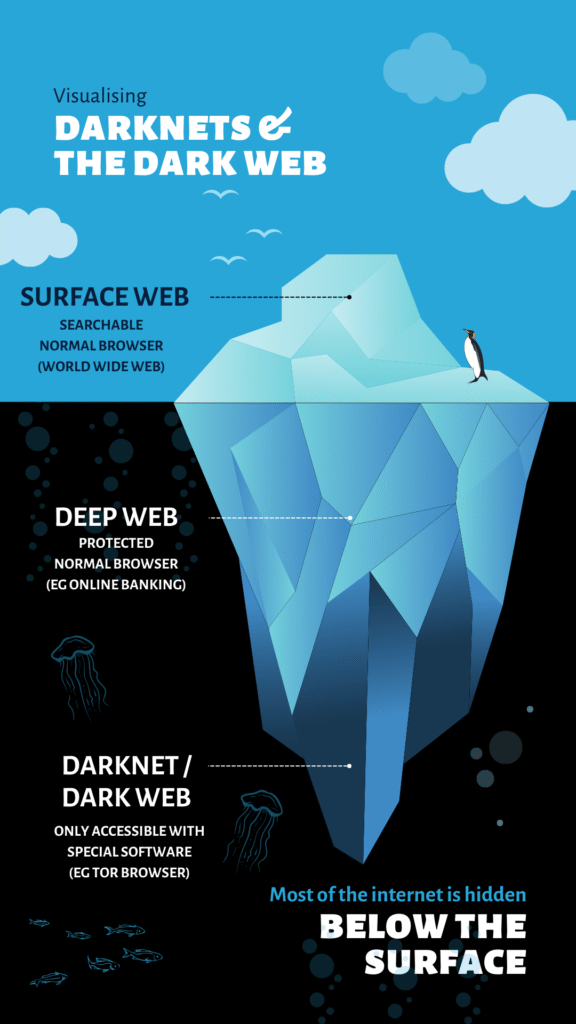
A darknet is an overlay network built on top of the regular internet but designed to provide anonymity and privacy to its users. Unlike the “surface web,” which is indexed by search engines, or even the “deep web,” which includes private databases and intranets, darknets require special software or configurations to access.
Examples include:
- Tor (The Onion Router): The most widely used darknet, famous for .onion domains.
- I2P (Invisible Internet Project): Focused on anonymous peer-to-peer communication.
- Freenet: Designed for censorship-resistant communication and file sharing.
- ZeroNet: A decentralized, Bitcoin-inspired platform for hosting websites.
These platforms route traffic through multiple relays or encrypted tunnels, obscuring user identity and location.
Darknets vs. The Dark Web
The terms “darknet” and “dark web” are often used interchangeably but are not identical.
- Darknet: The actual network infrastructure (e.g., Tor, I2P).
- Dark Web: The content hosted within these networks—websites, marketplaces, forums, and services.
This distinction is important. The darknet is a technology, while the dark web is an ecosystem that exists within it.
Legitimate Uses of Darknets
Although darknets are notorious for enabling cybercrime, they also serve legitimate and socially valuable purposes:
- Whistleblowing: Secure channels for journalists and activists (e.g., SecureDrop).
- Privacy Protection: Individuals in oppressive regimes use Tor to bypass censorship.
- Research: Cybersecurity and academic researchers study malware, threat actors, and underground economies.
- Personal Security: Users seeking to avoid pervasive tracking by corporations and governments.
Illicit Activity on Darknets
Unfortunately, darknets are also fertile ground for cybercriminal activity. Common illicit uses include:
- Darknet Marketplaces: Platforms like the defunct Silk Road, Hydra, and AlphaBay facilitated the sale of drugs, weapons, and counterfeit goods.
- Stolen Data and Credentials: Forums where breached databases, credit card dumps, and identity documents are traded.
- Malware-as-a-Service: Ransomware kits, exploit packs, and botnets for rent.
- Illegal Services: From contract hacking to human trafficking networks.
Transactions are typically conducted using cryptocurrencies like Bitcoin or Monero, which further obfuscate financial trails.
Security Risks for Users and Organizations
Darknets pose significant challenges for cybersecurity:
- Attack Surface Expansion: Employees accessing darknets can inadvertently introduce malware into corporate systems.
- Data Leakage: Sensitive organizational data (source code, intellectual property, customer PII) may appear on dark web forums.
- Credential Compromise: Leaked usernames and passwords fuel credential stuffing and phishing attacks.
- Evolving Threat Landscape: Cybercriminals adapt quickly, using decentralized hosting and new anonymization methods to evade takedowns.
Law Enforcement and Countermeasures
Despite their anonymity, darknets are not impenetrable:
- Traffic Correlation: Law enforcement agencies can sometimes de-anonymize users through sophisticated traffic analysis.
- Undercover Operations: Agencies infiltrate forums and marketplaces, gathering intelligence or conducting sting operations.
- Seizures: High-profile takedowns (e.g., Silk Road, AlphaBay) demonstrate that operators can be identified through operational mistakes.
- Commercial Monitoring Tools: Cyber threat intelligence (CTI) firms scan darknets for leaked data, alerting clients of breaches.
However, enforcement remains a game of cat-and-mouse, as new marketplaces or forums emerge after each takedown.
The Cybersecurity Professional’s Role
For defenders, darknets are both a threat vector and an intelligence resource:
- Threat Intelligence: Monitoring darknet activity helps organizations identify breaches early, track threat actors, and understand attacker tactics.
- Incident Response: Rapid detection of leaked credentials or intellectual property allows for faster mitigation.
- Policy and Training: Educating employees about risks of darknet browsing reduces the chance of accidental exposure.
- Ethical Research: Darknet study requires strict compliance with legal and ethical guidelines, ensuring researchers do not inadvertently participate in or encourage illicit trade.
Future Trends
Darknets will continue evolving alongside broader internet trends. Likely developments include:
- More Decentralization: Adoption of blockchain and distributed ledger technologies for hosting resilient services.
- Integration with AI: Both defenders and attackers may use AI for threat detection or automating illicit services.
- Enhanced Privacy Tools: Growing public awareness of surveillance may increase mainstream adoption of anonymizing networks.
- Greater Regulation: Governments may introduce stricter policies around anonymity services, with implications for civil liberties.
Conclusion
Darknets are not inherently “good” or “bad.” They are tools—capable of empowering free expression and privacy while simultaneously enabling serious cybercrime. For cybersecurity practitioners, darknets represent both a challenge and an opportunity. By understanding how darknets function, monitoring them responsibly, and integrating darknet intelligence into defensive strategies, organizations can stay ahead of emerging threats in these hidden corners of the internet.

