Mobile Device Security
When most people think about cybersecurity, their minds jump straight to firewalls, intrusion detection, encryption, and patch management. But there’s another dimension of security that often gets overlooked: physical security—particularly when it comes to mobile devices.
Addressing physical device security includes considering the set of policies, controls, and best practices that prevent theft, tampering, or unauthorised access to mobile devices such as smartphones, tablets, and laptops. Unlike purely digital defenses, physical safeguards ensure that attackers can’t simply bypass your network security by stealing the hardware itself.

Why Physical Security Matters for Mobile Devices
Mobile devices are powerful, portable, and pervasive. They carry vast amounts of sensitive organizational data and often serve as gateways into enterprise networks. Losing control of a device isn’t just an inconvenience—it can lead to catastrophic breaches.
Key threats include:
- Theft in public areas like airports, cafes, or conferences.
- Unauthorised access by insiders or strangers when devices are left unattended.
- Tampering or data exfiltration via direct connection (e.g., USB attacks, cloning).
- Environmental risks such as fire, flood, or physical damage.
In short, while encryption and authentication are essential, they are not enough if an attacker can simply walk off with an accessible device.
Elements of Physical Security for Mobile Devices
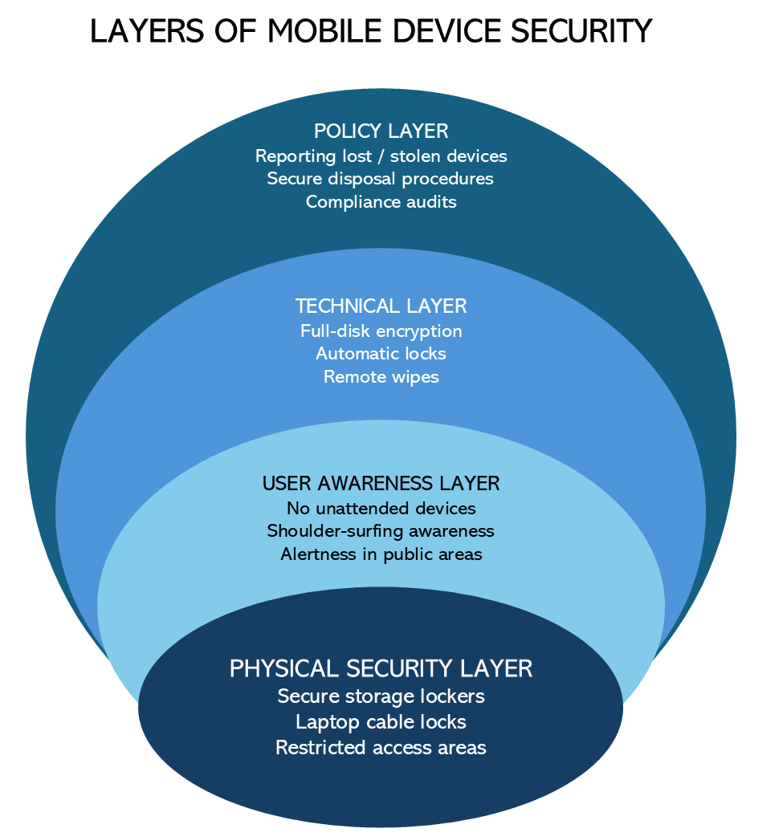
A strong physical security program for mobile devices typically includes the following components:
1. Physical Protection
- Store devices in secure areas (lockers, safes, or restricted-access offices).
- Use laptop cable locks or docking stations in shared spaces.
- Keep devices out of plain sight when unattended in vehicles or public areas.
2. User Awareness
- Train employees not to leave devices unattended.
- Encourage vigilance against shoulder surfing and opportunistic theft.
3. Technical Controls
- Enable full-disk encryption on all mobile devices.
- Configure automatic screen locks after inactivity.
- Deploy remote wipe capabilities to minimize data exposure if lost.
4. Environmental Safeguards
- Restrict use of mobile devices in sensitive environments (e.g., data centers).
- Enforce access controls and CCTV in offices where mobile devices are common.
5. Policy & Compliance
- Establish clear policies for reporting lost or stolen devices.
- Conduct regular audits of issued devices and their security status.
- Define procedures for secure device disposal.
Frameworks and Standards that Address Mobile Device Security
Physical security isn’t just common sense—it’s baked into leading cybersecurity frameworks and standards.
NIST SP 800-53 Rev. 5
- AC-19: Access Control for Mobile Devices requires organizations to physically safeguard devices, particularly when outside controlled areas.
- “Controlled environments” are defined as locations with physical or procedural protections, such as corporate offices with security staff or badge access.
NIST SP 800-124 Rev. 2
- Offers guidance for securing mobile devices throughout their lifecycle, from deployment to disposal.
- Addresses threats unique to mobile devices, including malware, unauthorized network access, and physical tampering.
CISA Guidance
- The Cybersecurity and Infrastructure Security Agency emphasizes protecting devices against physical compromise to prevent malicious tool installation, device cloning, or covert data exfiltration.
Physical Information Security (General)
- Recognizes the intersection of physical and information security: safeguarding devices from fire, natural disasters, theft, and sabotage complements encryption and access controls.
Comparison: Framework Perspectives on Mobile Device Security
| Framework / Guidance | Relevant Control / Guidance | Key Focus |
|---|---|---|
| NIST SP 800-53 Rev. 5 | AC-19: Access Control for Mobile Devices | Physical safeguarding of devices, especially outside controlled areas. |
| NIST SP 800-124 Rev. 2 | Mobile Device Lifecycle Security | Secure deployment, configuration, updates, and disposal. |
| CISA Guidance | Best Practices for Device Protection | Preventing theft, cloning, or malicious hardware/software installation. |
| Physical Information Security (General) | Intersection of physical & digital security | Protecting devices and storage from fire, disasters, theft, and sabotage. |
Practical Steps for Organizations
If your organization is developing or updating a Physical_Security_Mobile_Device policy, here are actionable steps to take:
- Define scope: Clarify which devices are covered—company-issued, BYOD, or both.
- Mandate encryption: Ensure all devices store data securely.
- Set handling rules: Require employees to keep devices within sight or locked when unattended.
- Plan for incidents: Establish rapid reporting and response for lost/stolen devices.
- Align with frameworks: Map your controls to NIST, ISO 27001, or CIS Controls.
- Test readiness: Run tabletop exercises simulating stolen devices and measure response.
Final Thoughts
Physical security may sound old-fashioned compared to AI-driven cyber defenses or advanced zero-trust architectures. Yet, a stolen laptop without a lock or encryption can undo millions in cybersecurity investment overnight.
By implementing robust device security—grounded in frameworks like NIST SP 800-53 and NIST SP 800-124, and supported by practical policies—you create a layered defense strategy that keeps both digital and physical threats in check.

